Don't Get Phished

Although the term “Identity theft” has been around since the 1960s, the computer age and the growth of the internet has led to its proliferation. “Phishing” is one aspect of identity theft. It relies on convincing the victim that they are interacting with a “trustworthy entity”, such as a corporation or known individual. Depending on the severity of the identity theft, it can be a minor nuisance or it could result in total decimation of your reputation and financial stability. Either way, it is a crime in most parts of the world.
Over the past few months, a person from China has posed as me. This unscrupulous person wrote to developers and media affiliates seeking access to beta releases of some games, exclusive tchotchkes, and press copies of other games. He then turned around and sold these on various websites.
This issue isn't related only to theft of games and items from developers. Many popular phishing campaigns try to obtain your login information by putting up fake web pages. Other thieves use malicious scripts that inject keyloggers, which are programs that record every keystroke you make. Other hackers try to learn your vital personal information to help that cousin you never knew you had in South Africa--at your expense, of course.
Be Observant
The best way for you to protect your business, game accounts, and financial information is to look first, act last. Due diligence can save you a lot of heartache. Check the “from” address of your emails. If the sender’s email address is not the same as the site from which he or she claims to be, it's likely a phishing campaign. Don’t click on any links!
The second telltale sign is when the links within a document appear to be from one place but actually go to another. If you hover your mouse over the links without clicking on them, you will see the real website link in your email client. Usually, it is located at the bottom left of the window.
Understanding Domain Names
Some common techniques include modifying real URLs (the website address) with slight changes. So bankofamerica.com becomes bankofamerica.ru. This fake domain name is owned by a malicious entity.
I will try to give you a little insight on how internet domain names work. There are 3 parts of a domain:
- The Sub-Domain - This is the prefix to the domain, and servers can be configured to handle them differently. For example: magazine.gaiscioch.com points to the magazine site while www.gaiscioch.com points at the community site. These can be created without needing to register a new domain. Any system administrator can create an unlimited number of these sub-domains on any existing domain. They also can point to entirely different places. For example, ts.gaiscioch.com points to a TeamSpeak server. The common mail.domain.com sub-domain points to a mail server.
- The Domain - This is the part between the dots. This is the cosmetic name of the site.
- The Top Level Domain (TLD) - This is the extension at the end of the domain. It can vary, and can include endings like .com, .org, .net, .edu, .info or one of over one hundred new cosmetic TLD's such as .company, .university, .food, .me, etc.
When you type http://www.gaiscioch.com/ into a web browser it sends a call out to the Top Level Domain server (such as .com) which asks for the location of gaiscioch. The TLD server replies with the address of the Domain Name Server (DNS) entry registered for gaiscioch.com. It then sends a request to the gaiscioch.com name server to find the location for the protocal (http, mail, ftp, etc) and www subdomain. This is how domain names work.
So bankofamerica.ru will send your data to a very different place than bankofamerica.com. The .ru TLD server would have an entirely different registration than the .com TLD server. So you would likely end up somewhere you really don't want to be.
Investigating the Phish
In my case, this gentleman from China used the email address @gaiscioch.org to pose to as @gaiscioch.com. Here's an example of what his message looked like:
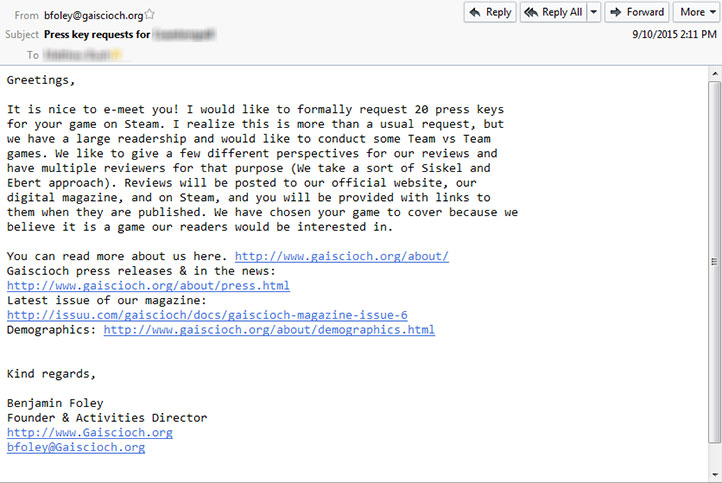
This looks very similar to something from the gaiscioch.com site, yes. However, there are some tricks I'll point out so you can recognize these spoofs.
First and foremost, the easiest way to check if something is legitimate is to use Google. Take off the .ext part (the .com, .org, .info, and other endings) and search the almighty Google with that website name. See what appears. If you search for Gaiscioch, you won’t find Gaiscioch.org anywhere. You will, however, find Gaiscioch.com. If the suspicious website doesn’t show up in the search results, it’s likely that it’s not legitimate.
The second thing you can do to check if a site is the real one is to use a tool to do an IP lookup of the sender. The IP (short for “Internet Protocol”) is a series of numbers that tells the internet where the website is based. To find this IP address go to View > Headers > All in your email application and you should see a lot more information than the simple To: and From:. Inside this massive amount of unreadable text you should see a few lines saying "Received:". You're looking for the one that says "authenticated user".
Example:
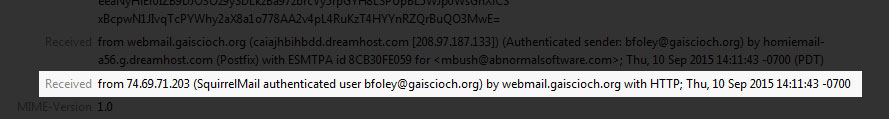
Now in this case, bfoley@gaiscioch.org is using his webmail account to access email that doesn't relay the end user IP address. It just relays the webmail server IP address 74.59.71.203. This can be anywhere in the world. In some cases you'll see a much more detailed description including the IP address 127.0.0.1, a long domain name (the internet service provider’s reserved address for that user), and an IP address in [brackets]. Any time you see 127.0.0.1, this is the loopback address which points back at yourself. If you were to attack 127.0.0.1 you would be attacking yourself. This is an indication that this IP address is the base machine that sent the email. In the case of WebMail-sent emails, you'll need to dig a little deeper to find their true location.
To locate a website’s true location, you can check the whois information for their domain by going to a site like MX Toolbox (http://mxtoolbox.com/SuperTool.aspx). You can type "whois:gaiscioch.org" into the search and see that it was registered by a man out of China.
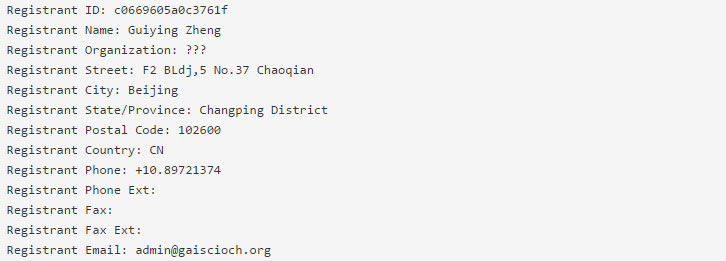
Now, the original "whois:gaiscioch.com" was registered by one "Benjamin Foley" out of Oregon. This is a dead giveaway that the websites are not the same and that the owner of gaiscioch.org is not who he claims to be.
Be Smart, Protect Your Assets
If you have any doubts about the authenticity of an email or other communication, reach out to the known contact from the official website you found on Google. It's better to ask first than to send off some press access keys or other valuable information to someone who will sell them or leak sensitive game information using someone else's name.
I can't tell you how many times I have approached a company and their reply was, "what happened to the assets we sent you already?" It's heartbreaking to see so many game developers get scammed out of their products. A little due diligence could go a long way in protecting their products and keeping their hard work out of the hands of malicious thieves. When in doubt, reach out.
P.S. Who says "Nice to E-Meet you" anyways! I mean really! Is this the 90's?
About the Author

Foghladha
Managing Editor
Foghladha founded the Gaiscioch Social Gaming Community in 2001 and has since been the founder & activities director for this well known community. His role has gone beyond just running the Gaming Community and now includes running the Athletics Program in Portland, Oregon, as well as acting as the Managing Editor of the Gaiscioch Magazine, and is the Lead Producer on the Gaiscioch Livestream Productions. Additionally he networks with game developers to form relationships between Gaiscioch and development studios.
His experience in publishing dates back to helping his Grandparents who operated a printing press for over 40 years. In high school and college Benjamin excelled in journalism and played an active part in the school newspaper. Foghladha currently works full time as the director of technology for a franchise trade publication & education company.
